1.1. 개요
DES/3DES 암호화 알고리즘을 library 로 구현한 것입니다.
ECB 방식의 block 단위의 암호화/복호화부분을 구현한 것입니다. CFB, OFB 방식도 구현한게 있기는 한데 해당 부분은 제외하고 ECB방식만 공개합니다.
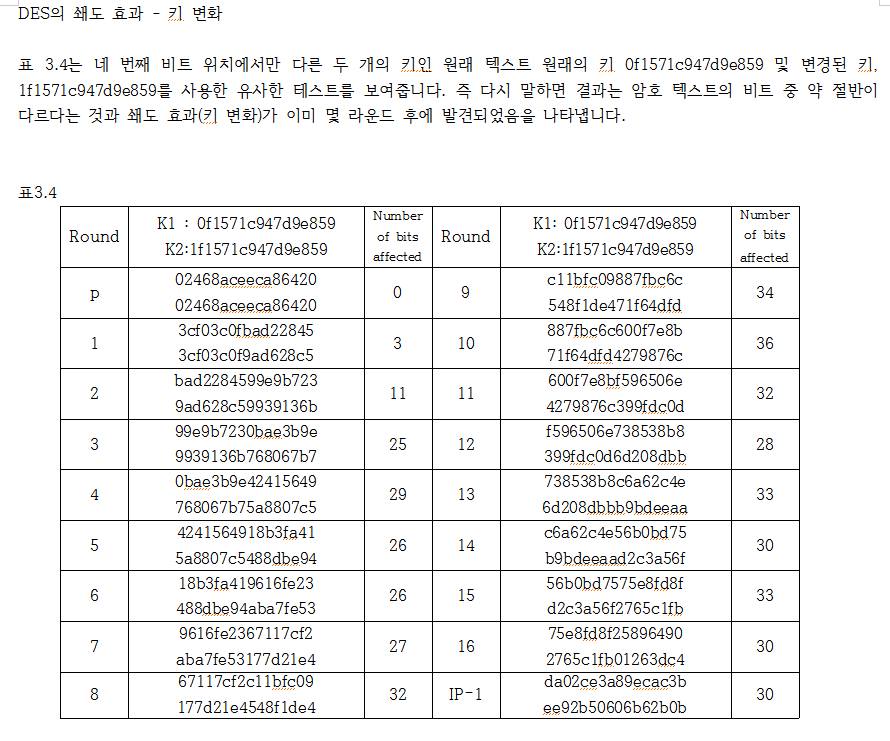
DES(Data Encryption Standard)는 블록 암호의 일종으로, 미국 NBS (National Bureau of Standards, 현재 NIST)에서 국가 표준으로 정한 암호화 알고리즘입니다. DES는 대칭키 암호이며, 56비트의 키를 사용합니다. DES는 현재 무차별 대입 공격을 하는 방식에 비교적 취약하다고 알려져 있어(비교적 짧은 시간에 해독이 가능하다고 알려짐) DES를 3회 반복하는 TripleDES가 이보다 안전한것으로 알려져 있습니다. 현재는 AES(Advanced Encryption Standard)가 새로운 표준으로 정해져 사용되는 추세입니다.
RSA사가 주관한 DES의 DES Challenge 결과 1997년의 DES ChallengeⅠ에서는 96일, 1998년의 DES Challenge Ⅱ-1에서는 41일, 1998년의 DES Challenge Ⅱ-2에서는 56시간, 1999년의 DES Challenge Ⅲ에서는 22시간 15분 만에 DES 키가 깨졌습니다.
ECB 방식의 block 단위의 암호화/복호화부분을 구현한 것입니다. CFB, OFB 방식도 구현한게 있기는 한데 해당 부분은 제외하고 ECB방식만 공개합니다.
DES(Data Encryption Standard)는 블록 암호의 일종으로, 미국 NBS (National Bureau of Standards, 현재 NIST)에서 국가 표준으로 정한 암호화 알고리즘입니다. DES는 대칭키 암호이며, 56비트의 키를 사용합니다. DES는 현재 무차별 대입 공격을 하는 방식에 비교적 취약하다고 알려져 있어(비교적 짧은 시간에 해독이 가능하다고 알려짐) DES를 3회 반복하는 TripleDES가 이보다 안전한것으로 알려져 있습니다. 현재는 AES(Advanced Encryption Standard)가 새로운 표준으로 정해져 사용되는 추세입니다.
RSA사가 주관한 DES의 DES Challenge 결과 1997년의 DES ChallengeⅠ에서는 96일, 1998년의 DES Challenge Ⅱ-1에서는 41일, 1998년의 DES Challenge Ⅱ-2에서는 56시간, 1999년의 DES Challenge Ⅲ에서는 22시간 15분 만에 DES 키가 깨졌습니다.
1.2. 사용권한
mzdes library source 는 수정없이 사용하신다면 누구나 그대로 사용하셔도 좋습니다.
단, source를 수정하셔서 사용하시려고 한다면 해당 수정사항에 대한 부분을 저에게 알려주시길 바랍니다.
1.3. 다운로드
1.4. 과정풀이
- 질문출처 :
![[https]](/moniwiki/imgs/https.png) https://www.facebook.com/photo.php?fbid=1122538724527526&set=gm.1420503504656848&type=3&theater
https://www.facebook.com/photo.php?fbid=1122538724527526&set=gm.1420503504656848&type=3&theater![[]](/moniwiki/imgs/moni2/external.png)
 [JPG image (101.8 KB)]
[JPG image (101.8 KB)]
- 결과
test des #1 ~~~~~~~~~~~ user key: 0F 15 71 C9 47 D9 E8 59 [..q.G..Y ] data: 02 46 8A CE EC A8 64 20 [.F....d ] IP round: 3C F0 3C 0F BA D2 28 45 [<.<...(E ] BA D2 28 45 99 E9 B7 23 [..(E...# ] 99 E9 B7 23 0B AE 3B 9E [...#..;. ] 0B AE 3B 9E 42 41 56 49 [..;.BAVI ] 42 41 56 49 18 B3 FA 41 [BAVI...A ] 18 B3 FA 41 96 16 FE 23 [...A...# ] 96 16 FE 23 67 11 7C F2 [...#g.|. ] 67 11 7C F2 C1 1B FC 09 [g.|..... ] C1 1B FC 09 88 7F BC 6C [.......l ] 88 7F BC 6C 60 0F 7E 8B [...l`.~. ] 60 0F 7E 8B F5 96 50 6E [`.~...Pn ] F5 96 50 6E 73 85 38 B8 [..Pns.8. ] 73 85 38 B8 C6 A6 2C 4E [s.8...,N ] C6 A6 2C 4E 56 B0 BD 75 [..,NV..u ] 56 B0 BD 75 75 E8 FD 8F [V..uu... ] 75 E8 FD 8F 25 89 64 90 [u...%.d. ] encrypt: E5 01 CD 35 46 DC 5C 37 [...5F.\7 ] test des #2 ~~~~~~~~~~~ user key: 1F 15 71 C9 47 D9 E8 59 [..q.G..Y ] data: 02 46 8A CE EC A8 64 20 [.F....d ] IP round: 3C F0 3C 0F 9A D6 28 C5 [<.<...(. ] 9A D6 28 C5 99 39 13 6B [..(..9.k ] 99 39 13 6B 76 80 67 B7 [.9.kv.g. ] 76 80 67 B7 5A 88 07 C5 [v.g.Z... ] 5A 88 07 C5 48 8D BE 94 [Z...H... ] 48 8D BE 94 AB A7 FE 53 [H......S ] AB A7 FE 53 17 7D 21 E4 [...S.}!. ] 17 7D 21 E4 54 8F 1D E4 [.}!.T... ] 54 8F 1D E4 71 F6 4D FD [T...q.M. ] 71 F6 4D FD 42 79 87 6C [q.M.By.l ] 42 79 87 6C 39 9F DC 0D [By.l9... ] 39 9F DC 0D 6D 20 8D BB [9...m .. ] 6D 20 8D BB B9 BD EE AA [m ...... ] B9 BD EE AA D2 C3 A5 6F [.......o ] D2 C3 A5 6F 27 65 C1 FB [...o'e.. ] 27 65 C1 FB 01 26 3D C4 ['e...&=. ] encrypt: DD 61 7A 09 09 79 17 07 [.az..y.. ] - 구현소스
/* Copyright (C) JAEHYUK CHO All rights reserved. Code by JaeHyuk Cho <mailto:minzkn@minzkn.com> DES 알고리즘의 쉐도효과(avalanche effect)에 대한 과정확인을 위해 구현된 소스 - 질문출처 : [^https://www.facebook.com/photo.php?fbid=1122538724527526&set=gm.1420503504656848&type=3&theater] */ #include <stdio.h> #include <stdlib.h> #include <string.h> #define __hwport_peek_f(m_cast,m_base,m_offset) ((m_cast)(((unsigned char *)(m_base)) + (m_offset))) #define __hwport_peek_const_f(m_cast,m_base,m_offset) ((m_cast)(((const unsigned char *)(m_base)) + (m_offset))) #define def_hwport_des_block_size 8 #define def_hwport_des_user_key_size def_hwport_des_block_size #define def_hwport_des_rounds 16 #define def_hwport_des_round_key_size (48 * def_hwport_des_rounds) void hwport_hex_dump(const char *s_title, const void *s_data, int s_size); void *hwport_des_block(int s_function, void *s_data, const void *s_round_key); void *hwport_des_make_round_key(void *s_round_key, const void *s_user_key); void des_avalanche_effect_test(unsigned char *s_user_key, unsigned char *s_data_block); int main(void); /* initial permutation table */ static int const __gc_hwport_des_ip_table[2][64] = { { 57, 49, 41, 33, 25, 17, 9, 1, 59, 51, 43, 35, 27, 19, 11, 3, 61, 53, 45, 37, 29, 21, 13, 5, 63, 55, 47, 39, 31, 23, 15, 7, 56, 48, 40, 32, 24, 16, 8, 0, 58, 50, 42, 34, 26, 18, 10, 2, 60, 52, 44, 36, 28, 20, 12, 4, 62, 54, 46, 38, 30, 22, 14, 6 }, { /* reverse */ 39, 7, 47, 15, 55, 23, 63, 31, 38, 6, 46, 14, 54, 22, 62, 30, 37, 5, 45, 13, 53, 21, 61, 29, 36, 4, 44, 12, 52, 20, 60, 28, 35, 3, 43, 11, 51, 19, 59, 27, 34, 2, 42, 10, 50, 18, 58, 26, 33, 1, 41, 9, 49, 17, 57, 25, 32, 0, 40, 8, 48, 16, 56, 24 } }; /* key permutation table */ static int const __gc_hwport_des_kp_table[56] = { 56, 48, 40, 32, 24, 16, 8, 0, 57, 49, 41, 33, 25, 17, 9, 1, 58, 50, 42, 34, 26, 18, 10, 2, 59, 51, 43, 35, 62, 54, 46, 38, 30, 22, 14, 6, 61, 53, 45, 37, 29, 21, 13, 5, 60, 52, 44, 36, 28, 20, 12, 4, 27, 19, 11, 3 }; /* key left shift table */ static unsigned char const __gc_hwport_des_kls_table[16] = { 0, 0, 1, 1, 1, 1, 1, 1, 0, 1, 1, 1, 1, 1, 1, 0 }; /* compression permutation table */ static int const __gc_hwport_des_cp_table[48] = { 13, 16, 10, 23, 0, 4, 2, 27, 14, 5, 20, 9, 22, 18, 11, 3, 25, 7, 15, 6, 26, 19, 12, 1, 40, 51, 30, 36, 46, 54, 29, 39, 50, 44, 32, 47, 43, 48, 38, 55, 33, 52, 45, 41, 49, 35, 28, 31 }; /* expansion permutation table */ static int const __gc_hwport_des_ep_table[48] = { 31, 0, 1, 2, 3, 4, 3, 4, 5, 6, 7, 8, 7, 8, 9, 10, 11, 12, 11, 12, 13, 14, 15, 16, 15, 16, 17, 18, 19, 20, 19, 20, 21, 22, 23, 24, 23, 24, 25, 26, 27, 28, 27, 28, 29, 30, 31, 0 }; /* S-Box substitution table */ static unsigned char const __gc_hwport_des_sbox_table[8][4][16] = { { /* S1 */ {14, 4, 13, 1, 2, 15, 11, 8, 3, 10, 6, 12, 5, 9, 0, 7}, { 0, 15, 7, 4, 14, 2, 13, 1, 10, 6, 12, 11, 9, 5, 3, 8}, { 4, 1, 14, 8, 13, 6, 2, 11, 15, 12, 9, 7, 3, 10, 5, 0}, {15, 12, 8, 2, 4, 9, 1, 7, 5, 11, 3, 14, 10, 0, 6, 13} }, { /* S2 */ {15, 1, 8, 14, 6, 11, 3, 4, 9, 7, 2, 13, 12, 0, 5, 10}, { 3, 13, 4, 7, 15, 2, 8, 14, 12, 0, 1, 10, 6, 9, 11, 5}, { 0, 14, 7, 11, 10, 4, 13, 1, 5, 8, 12, 6, 9, 3, 2, 15}, {13, 8, 10, 1, 3, 15, 4, 2, 11, 6, 7, 12, 0, 5, 14, 9} }, { /* S3 */ {10, 0, 9, 14, 6, 3, 15, 5, 1, 13, 12, 7, 11, 4, 2, 8}, {13, 7, 0, 9, 3, 4, 6, 10, 2, 8, 5, 14, 12, 11, 15, 1}, {13, 6, 4, 9, 8, 15, 3, 0, 11, 1, 2, 12, 5, 10, 14, 7}, { 1, 10, 13, 0, 6, 9, 8, 7, 4, 15, 14, 3, 11, 5, 2, 12} }, { /* S4 */ { 7, 13, 14, 3, 0, 6, 9, 10, 1, 2, 8, 5, 11, 12, 4, 15}, {13, 8, 11, 5, 6, 15, 0, 3, 4, 7, 2, 12, 1, 10, 14, 9}, {10, 6, 9, 0, 12, 11, 7, 13, 15, 1, 3, 14, 5, 2, 8, 4}, { 3, 15, 0, 6, 10, 1, 13, 8, 9, 4, 5, 11, 12, 7, 2, 14} }, { /* S5 */ { 2, 12, 4, 1, 7, 10, 11, 6, 8, 5, 3, 15, 13, 0, 14, 9}, {14, 11, 2, 12, 4, 7, 13, 1, 5, 0, 15, 10, 3, 9, 8, 6}, { 4, 2, 1, 11, 10, 13, 7, 8, 15, 9, 12, 5, 6, 3, 0, 14}, {11, 8, 12, 7, 1, 14, 2, 13, 6, 15, 0, 9, 10, 4, 5, 3} }, { /* S6 */ {12, 1, 10, 15, 9, 2, 6, 8, 0, 13, 3, 4, 14, 7, 5, 11}, {10, 15, 4, 2, 7, 12, 9, 5, 6, 1, 13, 14, 0, 11, 3, 8}, { 9, 14, 15, 5, 2, 8, 12, 3, 7, 0, 4, 10, 1, 13, 11, 6}, { 4, 3, 2, 12, 9, 5, 15, 10, 11, 14, 1, 7, 6, 0, 8, 13} }, { /* S7 */ { 4, 11, 2, 14, 15, 0, 8, 13, 3, 12, 9, 7, 5, 10, 6, 1}, {13, 0, 11, 7, 4, 9, 1, 10, 14, 3, 5, 12, 2, 15, 8, 6}, { 1, 4, 11, 13, 12, 3, 7, 14, 10, 15, 6, 8, 0, 5, 9, 2}, { 6, 11, 13, 8, 1, 4, 10, 7, 9, 5, 0, 15, 14, 2, 3, 12} }, { /* S8 */ {13, 2, 8, 4, 6, 15, 11, 1, 10, 9, 3, 14, 5, 0, 12, 7}, { 1, 15, 13, 8, 10, 3, 7, 4, 12, 5, 6, 11, 0, 14, 9, 2}, { 7, 11, 4, 1, 9, 12, 14, 2, 0, 6, 10, 13, 15, 3, 5, 8}, { 2, 1, 14, 7, 4, 10, 8, 13, 15, 12, 9, 0, 3, 5, 6, 11} } }; /* P-Box permutation table */ static int const __gc_hwport_des_pbox_table[32] = { 15, 6, 19, 20, 28, 11, 27, 16, 0, 14, 22, 25, 4, 17, 30, 9, 1, 7, 23, 13, 31, 26, 2, 8, 18, 12, 29, 5, 21, 10, 3, 24 }; /* inline function : bit to byte */ #define hwport_des_bit_to_byte(m_target,m_source,m_size) \ do {\ unsigned char *__sm_target__ = (unsigned char *)(m_target), __sm_byte__;\ const unsigned char *__sm_source__ = (const unsigned char *)(m_source);\ size_t __sm_size__ = ((size_t)(m_size)) << 3, __sm_offset__ = (size_t)0;\ do {\ __sm_byte__ = __sm_source__[__sm_offset__ >> 3];\ __sm_target__[__sm_offset__++] = (__sm_byte__ >> 7) & ((unsigned char)0x01);\ __sm_target__[__sm_offset__++] = (__sm_byte__ >> 6) & ((unsigned char)0x01);\ __sm_target__[__sm_offset__++] = (__sm_byte__ >> 5) & ((unsigned char)0x01);\ __sm_target__[__sm_offset__++] = (__sm_byte__ >> 4) & ((unsigned char)0x01);\ __sm_target__[__sm_offset__++] = (__sm_byte__ >> 3) & ((unsigned char)0x01);\ __sm_target__[__sm_offset__++] = (__sm_byte__ >> 2) & ((unsigned char)0x01);\ __sm_target__[__sm_offset__++] = (__sm_byte__ >> 1) & ((unsigned char)0x01);\ __sm_target__[__sm_offset__++] = (__sm_byte__ >> 0) & ((unsigned char)0x01);\ }while(__sm_offset__ < __sm_size__);\ }while(0) /* inline function : byte to bit */ #define hwport_des_byte_to_bit(m_target,m_source,m_size) \ do {\ unsigned char *__sm_target__ = (unsigned char *)(m_target), *__sm_source__ = (unsigned char *)(m_source), __sm_byte__ = (unsigned char)0;\ size_t __sm_size__ = (size_t)(m_size), __sm_offset__ = (size_t)0;\ while(__sm_offset__ < __sm_size__) {\ __sm_byte__ = (__sm_byte__ << 1) | __sm_source__[__sm_offset__++];\ if((__sm_offset__ % ((size_t)8)) != ((size_t)0)) { continue; }\ __sm_target__[(__sm_offset__ - ((size_t)1)) >> 3] = __sm_byte__;\ }\ }while(0) #define def_hwport_des_encrypt_function ((int)0) #define def_hwport_des_decrypt_function ((int)1) void hwport_hex_dump(const char *s_title, const void *s_data, int s_size) { int s_o,s_w,s_i;unsigned char s_b[17]; if(s_title != ((const char *)0)) { (void)printf("%s:\n", s_title); } s_b[16]='\0';s_o=(int)0; while(s_o<(s_size)){ s_w=((s_size)-s_o)<16?((s_size)-s_o):16;/* printf("%08X",s_o); */printf(" ");for(s_i=0;s_i<s_w;s_i++){if(s_i==8)printf(" | ");else printf(" "); s_b[s_i]=*(((const unsigned char *)(s_data))+s_o+s_i);printf("%02X",s_b[s_i]);if((s_b[s_i]>=0x7f)||(s_b[s_i]<' '))s_b[s_i]='.';} while(s_i<16){if(s_i==8)printf(" ");else printf(" ");s_b[s_i]=' ';s_i++;} printf(" [%s]\n",(char *)s_b);s_o+=16;} #if 0L (void)printf("\n"); #endif } void *hwport_des_block(int s_function, void *s_data, const void *s_round_key) { unsigned char s_temp[64], s_ip[64], s_next_left[32], s_ep[48], *s_left, *s_right, *s_ep_ptr, s_value; int s_index, s_round; /* bit to byte */ hwport_des_bit_to_byte(&s_temp[0], s_data, 8); /* initial permutation */ for(s_index = (int)0;s_index < ((int)64);s_index++) { s_ip[s_index] = s_temp[__gc_hwport_des_ip_table[0][s_index]]; } /* left & right */ if(s_function == def_hwport_des_encrypt_function) { s_left = (unsigned char *)(&s_ip[0]); s_right = (unsigned char *)(&s_ip[32]); } else { s_left = (unsigned char *)(&s_ip[32]); s_right = (unsigned char *)(&s_ip[0]); } /* 16 round loop */ for(s_round = (int)0;s_round < ((int)def_hwport_des_rounds);s_round++) { /* backup right(next left) */ for(s_index = (int)0;s_index < ((int)32);s_index++) { s_next_left[s_index] = s_right[s_index]; } /* expansion permutation with xor */ if(s_function == def_hwport_des_encrypt_function) { /* spinning direction key */ for(s_index = (int)0;s_index < ((int)48);s_index++) { s_ep[s_index] = s_right[__gc_hwport_des_ep_table[s_index]] ^ (*__hwport_peek_const_f(const unsigned char *, s_round_key, (s_round * ((int)48)) + s_index)); } } else { /* reverse direction key */ for(s_index = (int)0;s_index < ((int)48);s_index++) { s_ep[s_index] = s_right[__gc_hwport_des_ep_table[s_index]] ^ (*__hwport_peek_const_f(const unsigned char *, s_round_key, ((((int)(def_hwport_des_rounds - 1)) - s_round) * ((int)48)) + s_index)); } } /* S-Box substitution */ for(s_index = (int)0;s_index < ((int)8);s_index++) { s_ep_ptr = (unsigned char *)(&s_ep[s_index * ((int)6)]); s_value = __gc_hwport_des_sbox_table[s_index][(s_ep_ptr[0] << 1) | s_ep_ptr[5]][(s_ep_ptr[1] << 3) | (s_ep_ptr[2] << 2) | (s_ep_ptr[3] << 1) | s_ep_ptr[4]]; s_temp[(s_index << 2) + ((int)0)] = (s_value >> 3) & ((unsigned char)0x01); s_temp[(s_index << 2) + ((int)1)] = (s_value >> 2) & ((unsigned char)0x01); s_temp[(s_index << 2) + ((int)2)] = (s_value >> 1) & ((unsigned char)0x01); s_temp[(s_index << 2) + ((int)3)] = (s_value >> 0) & ((unsigned char)0x01); } /* P-Box permutation */ for(s_index = (int)0;s_index < ((int)32);s_index++) { s_right[s_index] = s_temp[__gc_hwport_des_pbox_table[s_index]] ^ s_left[s_index]; s_left[s_index] = s_next_left[s_index]; } #if 1L /* IP round dump for avalanche effect ###################### */ do { unsigned char s_data2[ def_hwport_des_block_size ]; if(s_round == 0) { (void)printf("IP round:\n"); } hwport_des_byte_to_bit(s_data2, &s_ip[0], 64); hwport_hex_dump((const char *)0, s_data2, sizeof(s_data2)); }while(0); #endif } /* merge left & right */ if(s_function == def_hwport_des_encrypt_function) { for(s_index = (int)0;s_index < ((int)32);s_index++) { s_temp[s_index] = s_left[s_index]; s_temp[s_index + ((int)32)] = s_right[s_index]; } } else { for(s_index = (int)0;s_index < ((int)32);s_index++) { s_temp[s_index] = s_right[s_index]; s_temp[s_index + ((int)32)] = s_left[s_index]; } } /* reverse initial permutation */ for(s_index = (int)0;s_index < ((int)64);s_index++) { s_ip[s_index] = s_temp[__gc_hwport_des_ip_table[1][s_index]]; } /* byte to bit */ hwport_des_byte_to_bit(s_data, &s_ip[0], 64); return(s_data); } void *hwport_des_make_round_key(void *s_round_key, const void *s_user_key) { unsigned char s_temp[64], s_key56[56]; int s_index, s_round; /* bit to byte */ hwport_des_bit_to_byte(&s_temp[0], s_user_key, 8); /* key permutation */ for(s_index = (int)0;s_index < ((int)56);s_index++) { s_key56[s_index] = s_temp[__gc_hwport_des_kp_table[s_index]]; } for(s_round = (int)0;s_round < ((int)def_hwport_des_rounds);s_round++) { if(__gc_hwport_des_kls_table[s_round] == ((unsigned char)0)) { /* left (shift) rotate 1 */ s_temp[0] = s_key56[0]; s_temp[1] = s_key56[28]; for(s_index = (int)0;s_index < ((int)27);s_index++) { s_key56[s_index] = s_key56[s_index + ((int)1)]; s_key56[s_index + ((int)28)] = s_key56[s_index + ((int)(28 + 1))]; } s_key56[27] = s_temp[0]; s_key56[28 + 27] = s_temp[1]; } else { /* left (shift) rotate 2 */ s_temp[0] = s_key56[0]; s_temp[1] = s_key56[1]; s_temp[2] = s_key56[28]; s_temp[3] = s_key56[28 + 1]; for(s_index = (int)0;s_index < ((int)26);s_index++) { s_key56[s_index] = s_key56[s_index + ((int)2)]; s_key56[s_index + ((int)28)] = s_key56[s_index + ((int)(28 + 2))]; } s_key56[26] = s_temp[0]; s_key56[27] = s_temp[1]; s_key56[28 + 26] = s_temp[2]; s_key56[28 + 27] = s_temp[3]; } /* compression permutation */ for(s_index = (int)0;s_index < ((int)48);s_index++) { *__hwport_peek_f(unsigned char *, s_round_key, (s_round * ((int)48)) + s_index) = s_key56[__gc_hwport_des_cp_table[s_index]]; } } return(s_round_key); } void des_avalanche_effect_test(unsigned char *s_user_key, unsigned char *s_data_block) { unsigned char s_round_key[ def_hwport_des_round_key_size ]; /* (16 * 48) bytes */ hwport_hex_dump("user key", &s_user_key[0], sizeof(s_user_key)); (void)hwport_des_make_round_key(&s_round_key[0], &s_user_key[0]); #if 0 /* show round key */ do { int s_index0, s_index1, s_index2; (void)printf("round key:\n"); for(s_index0 = 0;s_index0 < def_hwport_des_rounds;s_index0++) { (void)printf("[%2d] ", s_index0); for(s_index1 = 0;s_index1 < 48;s_index1 += 8) { for(s_index2 = 0;s_index2 < 8;s_index2++) { (void)printf("%d", (unsigned int)s_round_key[s_index0 + s_index1 + s_index2]); } (void)printf("b "); } (void)printf("\n"); } (void)printf("\n"); }while(0); #endif hwport_hex_dump("data", &s_data_block[0], def_hwport_des_block_size); hwport_hex_dump("encrypt", hwport_des_block(def_hwport_des_encrypt_function, s_data_block, &s_round_key[0]), (size_t)def_hwport_des_block_size ); #if 0L hwport_hex_dump("decrypt", hwport_des_block(def_hwport_des_decrypt_function, s_data_block, &s_round_key[0]), (size_t)def_hwport_des_block_size ); #endif } int main(void) { unsigned char s_user_key[2][ def_hwport_des_user_key_size ] = { /* password */ {0x0f, 0x15, 0x71, 0xc9, 0x47, 0xd9, 0xe8, 0x59}, {0x1f, 0x15, 0x71, 0xc9, 0x47, 0xd9, 0xe8, 0x59} }; char s_data_block[2][def_hwport_des_block_size] = { /* plain text */ {0x02, 0x46, 0x8a, 0xce, 0xec, 0xa8, 0x64, 0x20}, {0x02, 0x46, 0x8a, 0xce, 0xec, 0xa8, 0x64, 0x20} }; int s_test_seq; for(s_test_seq = 0;s_test_seq < 2;s_test_seq++) { (void)printf("test des #%d\n~~~~~~~~~~~\n\n", s_test_seq + 1); des_avalanche_effect_test( (unsigned char *)(&s_user_key[s_test_seq][0]), (unsigned char *)(&s_data_block[s_test_seq][0]) ); } return(EXIT_SUCCESS); } /* vim: set expandtab: */ /* End of source */
